Firewall Considerations in Zerto Cloud Manager
When Zerto is installed on multiple sites, a Zerto Cloud Manager can be used to manage all the sites from one pane of glass for management, orchestration, reporting, and monitoring of recovery operations.
To ensure that all components communicate together successfully, both within a site and across sites, certain ports must be open. The required ports differ depending on which of the two types of architecture are used.
Zerto ICDR Architecture
The following diagram shows the basic Intra Cloud Disaster Recovery (ICDR) architecture with the required ports. ICDR organizations can manage their disaster recovery via the Zerto Self-service Portal.
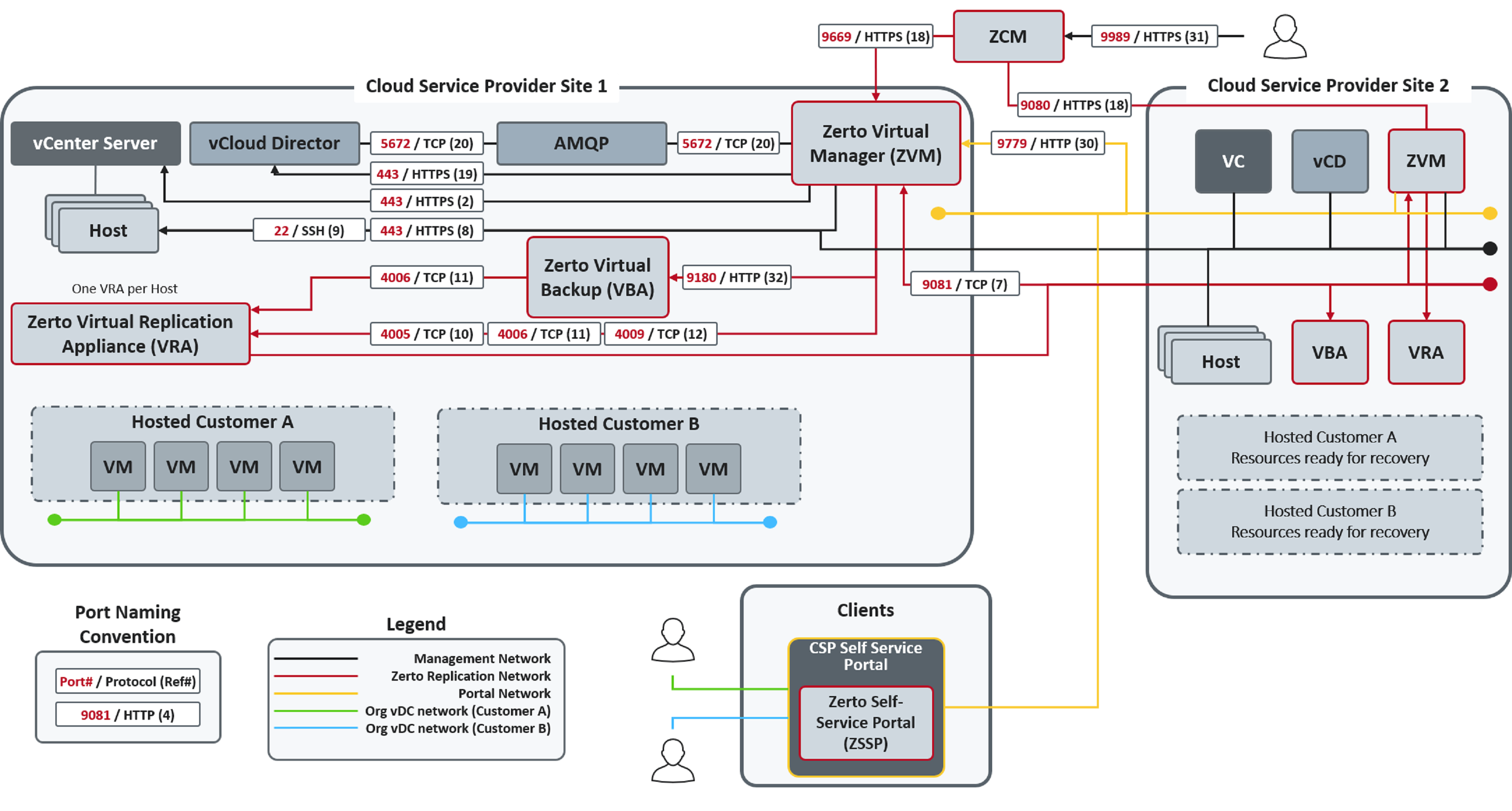
Zerto DRaaS Architecture
The following diagram shows the basic Data Recovery as a Service (DRaaS) architecture for a VMware environment, with the required ports. DRaaS organizations can manage their disaster recovery via the Zerto User Interface.
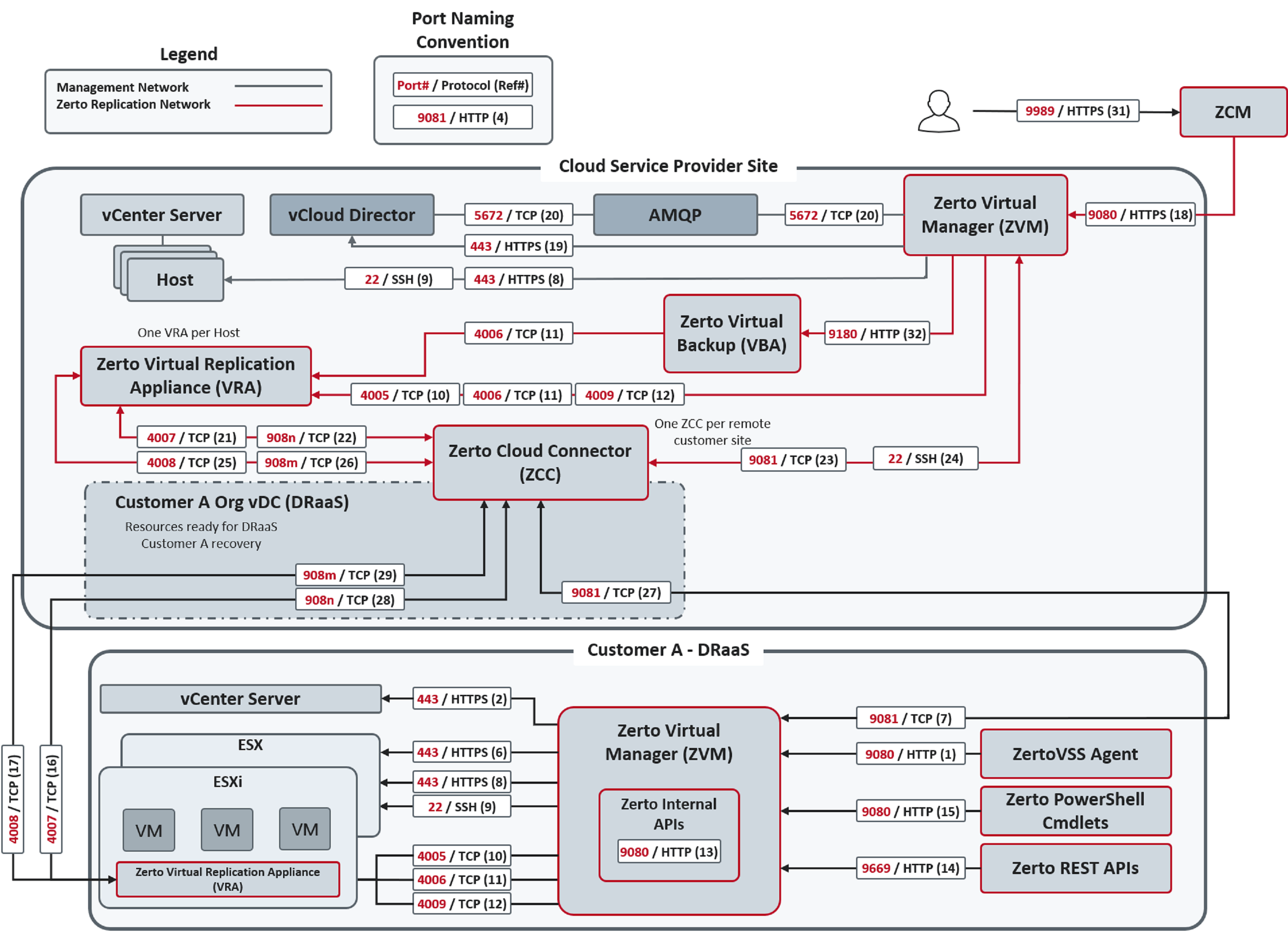
The following ports must be opened in the firewalls in both the organization and Managed Service Provider sites.
| Port | Description | |||||||||
| 22 | During Virtual Replication Appliance (VRA) installation on ESXi 5.1 and higher for communication between the Zerto Virtual Manager (ZVM) and the ESXi hosts IPs and for ongoing communication between the ZVM in the cloud site – but not the customer site – and a Zerto Cloud Connector. | |||||||||
| 443 | During VRA installation on ESX/ESXi hosts for communication between the ZVM and the ESX/ESXi hosts IPs and for ongoing communication between the ZVM and vCenter Server and vCloud Director. | |||||||||
| 4005 | Log collection between the Zerto Virtual Manager and Virtual Replication Appliances on the same site , using TLS over TCP communication. | |||||||||
| 4006 | TLS over TCP communication between the Zerto Virtual Manager and Virtual Replication Appliances on the same site. | |||||||||
| 4007 | Unencrypted TCP control communication between protecting and recovering VRAs and between a Zerto Cloud Connector and VRAs. | |||||||||
| 4008 | Unencrypted TCP communication between VRAs to pass data from protected virtual machines to a VRA on a recovery site and between a Zerto Cloud Connector and VRAs. | |||||||||
| 4009 | TLS over TCP communication between the Zerto Virtual Manager and site Virtual Replication Appliances to handle checkpoints. | |||||||||
| 7073 |
Internal port, used only on the ZVM VM. Used for communication with the service in charge of collecting data for the Zerto Resource Planner. Note: Unless you select the checkbox ‘Enable Support notification and product improvement feedback’, data is not transmitted to Zerto Analytics. |
|||||||||
| 8100 | Communication between the Zerto Virtual Manager and the System Center Virtual Machine Manager in a customer site running Zerto Virtual Replication with Hyper-V. | |||||||||
| 9071* | HTTPS communication between paired ZVMs. | |||||||||
| 8883 | MQTT communication between the ZVM and vCloud Director. | |||||||||
| 9080 |
|
|||||||||
| 9007 | Encrypted TCP control communication between protecting and recovering VRAs and between a Zerto Cloud Connector and VRAs. | |||||||||
| 9008 | Encrypted TCP communication between VRAs to pass data from protected virtual machines to a VRA on a recovery site and between a Zerto Cloud Connector and VRAs. | |||||||||
| 9071* | HTTPS communication between paired ZVMs. | |||||||||
| 9080 |
|
|||||||||
| 9081 |
TCP communication between Zerto Virtual Managers and between a customer Zerto Virtual Manager and a Zerto Cloud Connector, maintained for backward compatibility purposes. This port must not be changed when providing DRaaS. |
|||||||||
| 9072 to 9079, 9082 and up |
Two ports for each VRA (one for port 4007 and one for port 4008) accessed via the Zerto Cloud Connector installed by the Managed Service Provider.
For example: If Customer A network has 3 VRAs and customer B network has 2 VRAs and the Managed Service Provider management network has 4 VRAs, then the following ports must be open in the firewall for each cloud: The Managed Service Provider's VRAs need to use 12 ports to reach customer A's VRAs, while customer A's VRAs need 16 ports to reach the cloud's VRAs. The Managed Service Provider's VRAs need to use 8 ports to reach customer B's VRAs, while customer B's VRAs need 16 ports to reach the cloud's VRAs. |
|||||||||
| 9180 | Communication between the VBA and VRA. | |||||||||
| 9669 |
HTTPS communication between:
|
|||||||||
| 9779 | HTTPS communication between the Zerto Self-Service Portal for in-cloud (ICDR) customers and a ZVM. | |||||||||
| 9989 | HTTPS communication between the browser and the Zerto Cloud Manager. |