Design Considerations for DRaaS
The organization, defined in the Zerto Cloud Manager as a ZORG, Zerto Organization, connects to the Managed Service Provider via VPN, to a network that has a connection to the Internet or to a wider network that enables a connection between the cloud site and the customer site.
All the traffic to and from the customer is routed through a Zerto Cloud Connector.
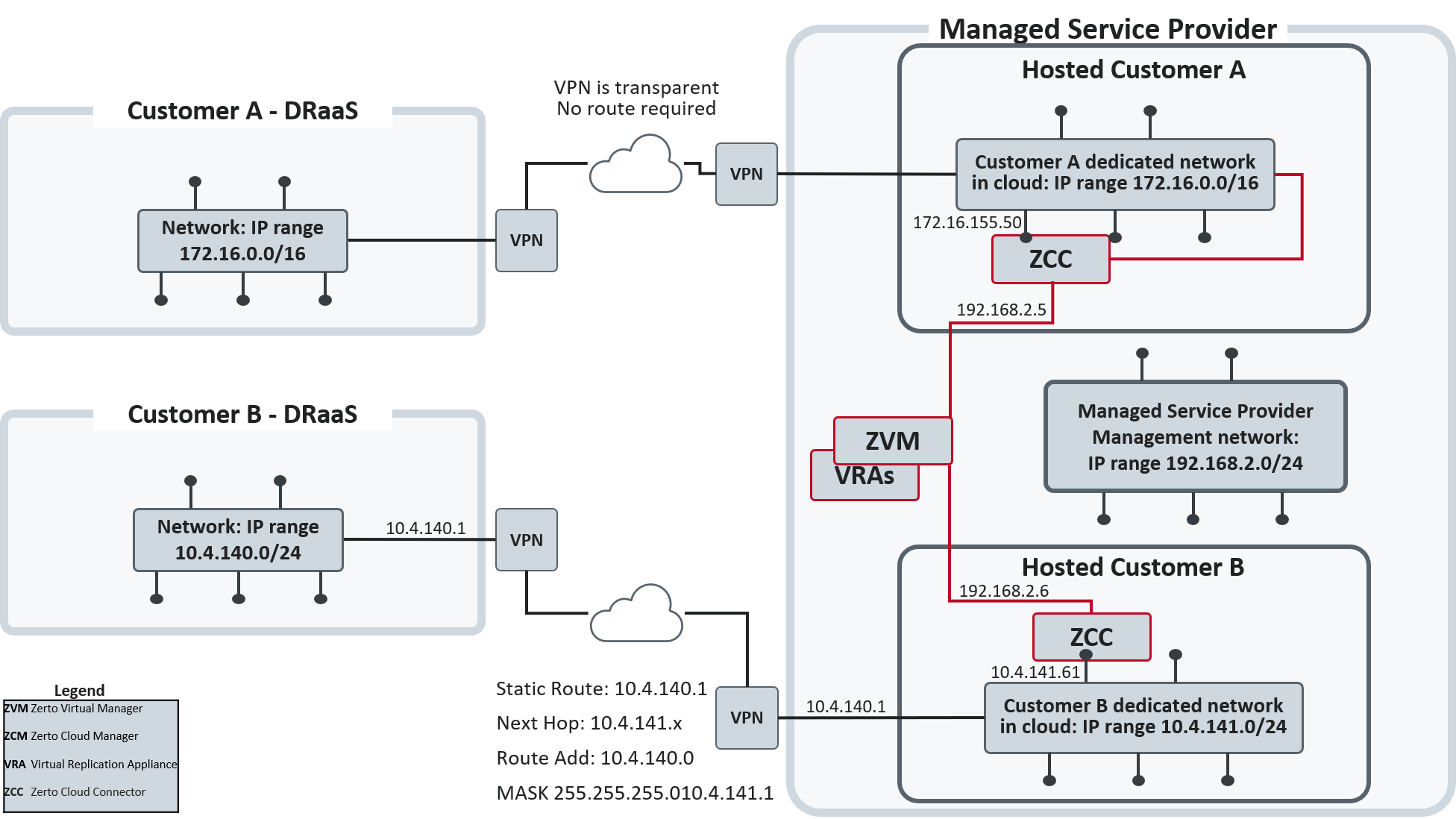
A cloud connector is a virtual machine installed on the cloud side, one for each customer replication network. The cloud connector has two Ethernet interfaces, one to the customer's network and one to the Managed Service Provider's network. Within the cloud connector a bidirectional connection is created between the customer and Managed Service Provider management networks. Thus, all network traffic passes through the cloud connector, where the incoming traffic on the customer network is automatically configured to IP addresses of the Managed Service Provider management network.
The Zerto Cloud Connectors ensure the following:
| • | None of the customers have direct access to the Managed Service Provider management network and cannot see any part of the Managed Service Provider management network that the Managed Service Provider does not allow them to see. |
| • | Each customer has no access to the network of another organization. |
If the Managed Service Provider wants to institute additional security, considering both cloud connector interfaces as part of the customer network, they can define a static route that will hop to a different cloud network, specifically for use by the Zerto Virtual Manager and VRAs in the cloud site.
The Zerto Cloud Connector requires both cloud-facing and customer-facing static IP addresses.
Also, for the cloud connector, the IP ranges used for the organization network and Managed Service Provider infrastructure network cannot be the same.
The cloud connector requires 2GB of disk space.
See also:
| • | Design Considerations for ICDR |